Pin - CTFLearn
Pin
DESCRIPTION : Can you crack my pin?
Basic Info
File command

It is 64 Bit elf binary
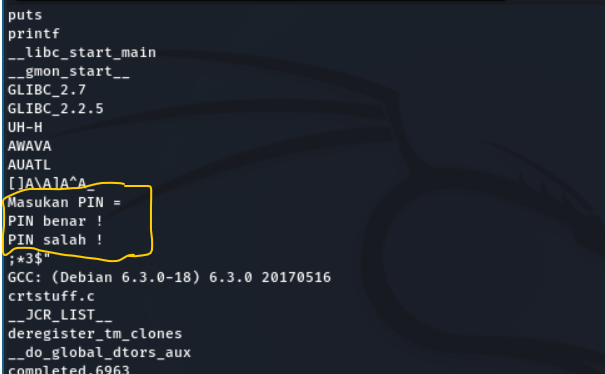
Strings command
There is some interesting strings.
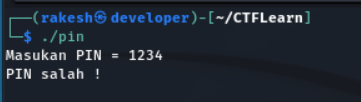
Run the binary
- It ask for the pin
- Then print PIN salah ( wrong pin )
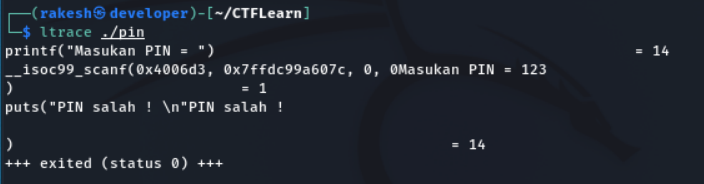
Ltrace command
There is no interesting libraries call like strcmp
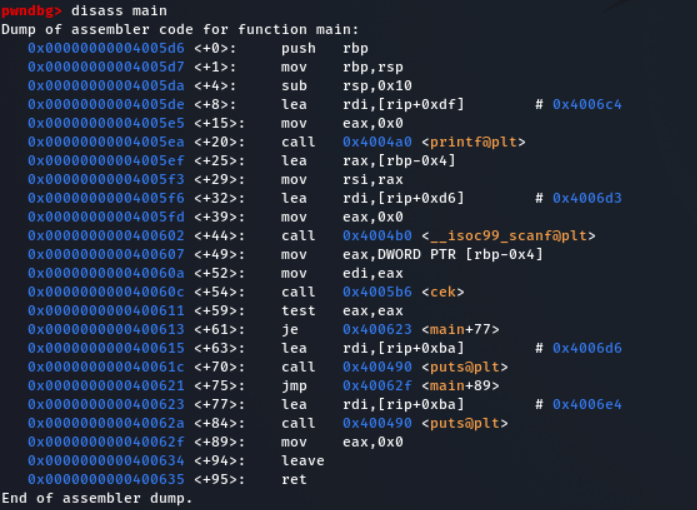
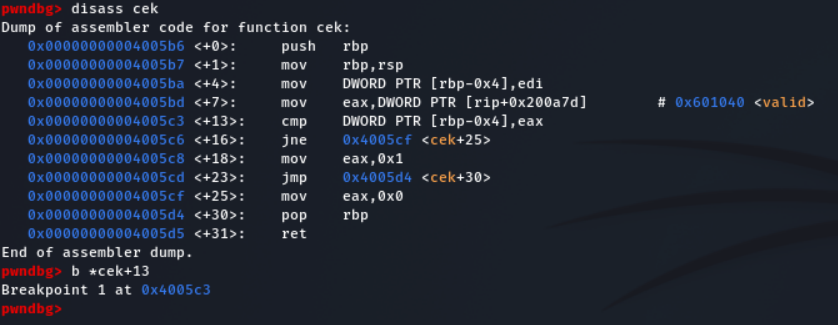
Let's analysis the binary in GDB
- Disassemble the main function
- It print the "Masukan PIN = "
- Then ask for the pin
- It call the cek function with argument of input
- Disassemble the cek function
- It compare the input with some value.
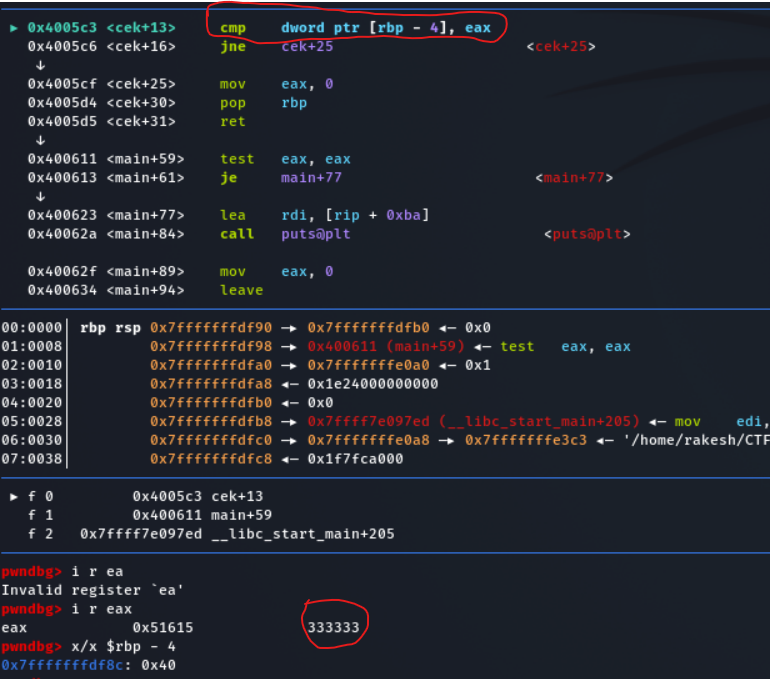
- Let's find the value by setting breakpoint at cmp statement
- Let's find the value
- Breakpoint hits, examine the value of eax
- The value of eax register is 333333
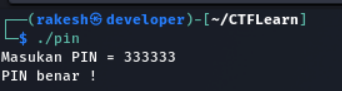
Yeah!!!! The pin is 333333.
The flag is CTFLearn{333333}